




One-time assessments provide actionable insight into your true risk exposure. They're designed to test defenses, not just check boxes. Simulate real-world attacks to uncover hidden vulnerabilities across your infrastructure, applications, and personnel.

Ongoing protection, governance, and support - delivered through 24/7 threat monitoring, MDR, SOC services, and compliance readiness. Designed to adapt to attacker behavior, close visibility gaps, and harden your environment over time.

Address the security challenges that matter most - operational resilience, data integrity, and long-term risk reduction.
Reveal how attackers would break in - not in theory, but in practice. Gain clarity on true risk and turn findings into actionable defense improvements.
DiscoverSee your organization from an attacker’s perspective. Identify exposed data and early warning signs to stay ahead of targeted threats.
DiscoverUnderstand how people - not just systems - impact your security posture. Uncover behavioral gaps that attackers routinely exploit.
DiscoverBuild secure software from the ground up. Detect vulnerabilities before deployment to reduce patch cycles, audit friction, and exploitability.
DiscoverEnsure cloud agility doesn’t come at the cost of exposure. Improve visibility, reduce misconfigurations, and align cloud practices with enterprise security goals.
DiscoverExpose weaknesses before attackers do. Silent Breach hunts down hidden flaws and delivers a clear roadmap to resilience.
DiscoverThreats move fast - so should your response. Our AI-powered security platform, Silent Armor, turns continuous monitoring and dark web threat intelligence into actionable security briefs, enabling your team to predict, prioritize, and eliminate threats in real time.
Learn more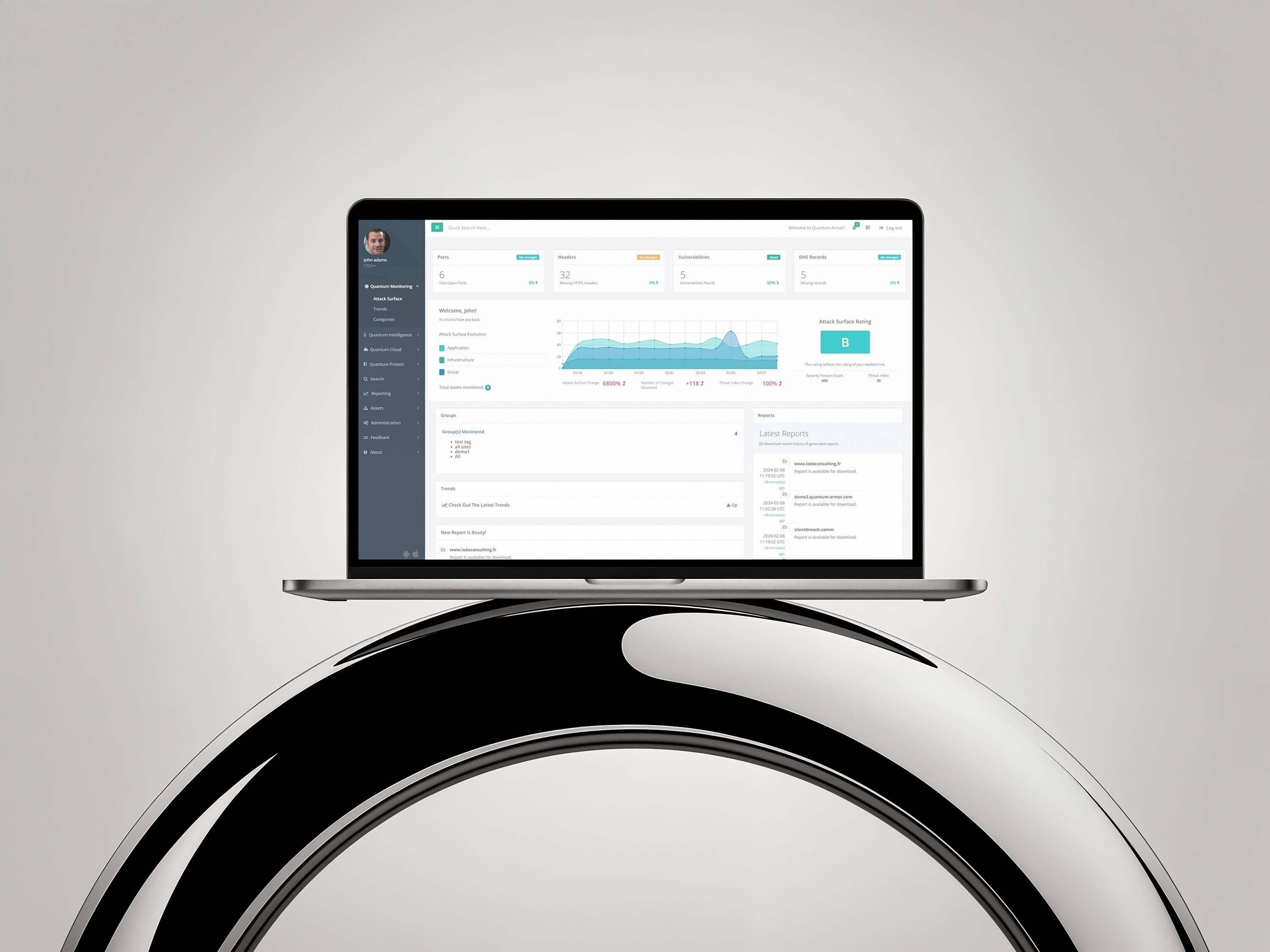






























Within 4 weeks, they plugged the holes in our customer's firewall and tweaked our application server. It's been working like a charm ever since!
Outstanding service executed in a timely manner. I would definitely recommend Silent Breach to anybody that truly wants to secure their business.
Within one hour of penetration testing, the red team already discovered three separate breaches. I had no idea how badly we were exposed. Thanks, Silent Breach!
Silent Breach's social engineering simulation exposed weaknesses we fixed within weeks, cutting insider risk dramatically.
Silent Breach gave us the intelligence and remediation steps we needed to shut those exposures down immediately.
Within 4 weeks, they plugged the holes in our customer's firewall and tweaked our application server. It's been working like a charm ever since!
Outstanding service executed in a timely manner. I would definitely recommend Silent Breach to anybody that truly wants to secure their business.
Within one hour of penetration testing, the red team already discovered three separate breaches. I had no idea how badly we were exposed. Thanks, Silent Breach!
Within one hour of penetration testing, the red team already discovered three separate breaches. I had no idea how badly we were exposed. Thanks, Silent Breach!
Silent Breach's social engineering simulation exposed weaknesses we fixed within weeks, cutting insider risk dramatically.
Silent Breach gave us the intelligence and remediation steps we needed to shut those exposures down immediately.

Get the latest security insights, threat updates, and exclusive offers - straight to your inbox.